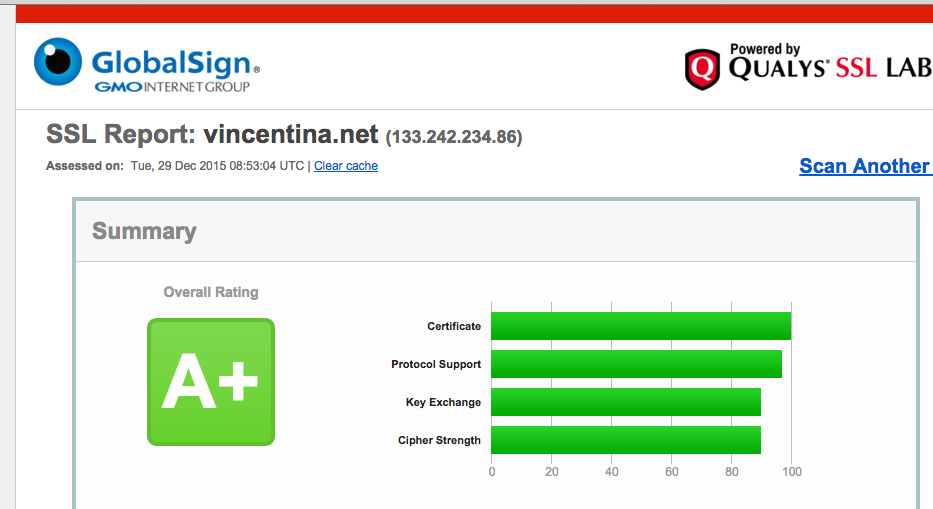
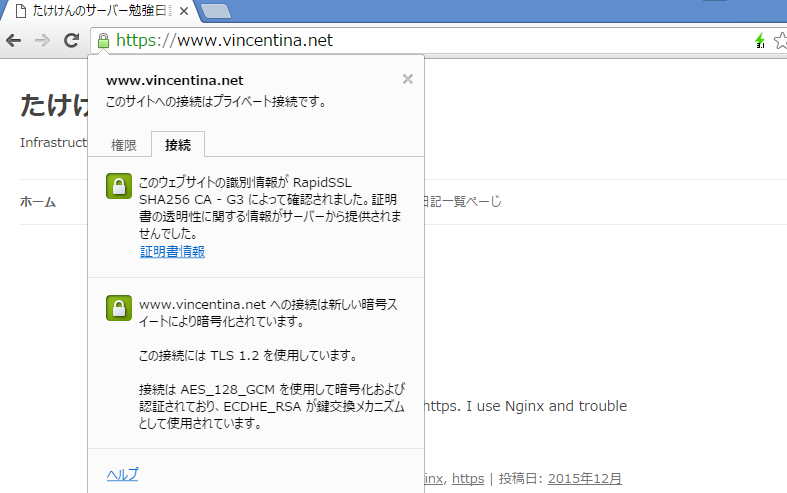
The last time, My web site became HTTPS. However, according to SSL SERVER, it was scored B+. Disappointed. So that, I’ll consider at a ssl.conf, I think I want to enhance security connections. The result, I was able to increase to A+. And I introduce some of the examples.
First, I was enabled SPDY. But this is NOT related to security.
listen 443 ssl; listen 443 ssl spdy;
Now, Spdy is enabled.
Now then, although I am saying reviewed ssl.conf I need reference materials.
I found “Mozilla SSL Configuration Generator“.
This is outputted a ssl.conf to fit each environment. For example, Nginx, set of modern and SSL 1.01e version. etc..
Second, about a ssl_ciphers.
Apparently ECDHE-RSA-AES128-GCM-SHA256 is newer.
Because
ssl_ciphers ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!3DES:!MD5:!PSK;
Priority is high that it is written to the left.
If you use a generator, it would include “DHE-RSA-AES128-GCM-SHA256”, but I have removed it. so that, so that, also, I didn’t create a dhparam.
Third, about an OCSP Stapling.
This is needed root CA certificate.
like this.
-----BEGIN CERTIFICATE----- Root CA Certificate -----END CERTIFICATE----- -----BEGIN CERTIFICATE----- Intermediate Certificate -----END CERTIFICATE-----
ssl.conf
# OCSP Stapling ---
# fetch OCSP records from URL in ssl_certificate and cache them
ssl_stapling on;
ssl_stapling_verify on;
ssl_trusted_certificate ca-certs.pem;
That’s it.
How was it.
Have a good day!
These are references.
My Library
http://blog.mylibs.jp/archives/181
Related Posts
- Automatic nightly WordPress updates CHECK with WP-CLI plugins
- What’s happened when altered to HHVM from PHP?
- To change Google language settings from Japanese to English may be useful to study English.